Are you tired of dealing with unauthorized access to your web applications? Look no further than the Application Load Balancer (ALB) from Amazon Web Services. Not only can an ALB balance traffic across multiple targets but it can also be used to authenticate users before granting access to your application. In this blog post, we will explore how an ALB can be used for authentication and the advantages and disadvantages of using this method. So sit tight and get ready to learn how you can beef up security on your web application with an ALB!
What is an Application Load Balancer?
An Application Load Balancer (ALB) is a type of load balancer that operates at the application layer and can distribute incoming traffic to multiple targets such as EC2 instances and containers. The ALB offers advanced routing capabilities that enable you to route requests based on rules or conditions.
One of the key features of an ALB is its ability to support WebSocket connections for real-time communication between clients and servers. An ALB also supports the HTTP/2 protocol, which provides faster page loading times and improved security over HTTPS.
The ALB integrates with Amazon Certificate Manager (ACM), allowing you to easily manage SSL/TLS certificates for secure communication between users and your web applications.
In addition, an ALB allows you to monitor the health status of your targets using a feature called target groups. This enables you to detect unhealthy targets in real-time and redirect traffic accordingly.
An Application Load Balancer provides powerful capabilities for optimizing performance, scaling your application infrastructure horizontally, improving security, monitoring health checks, and supporting modern protocols like WebSockets and HTTP/2 while being cost-effective.
How can an Application Load Balancer be used to authenticate users?
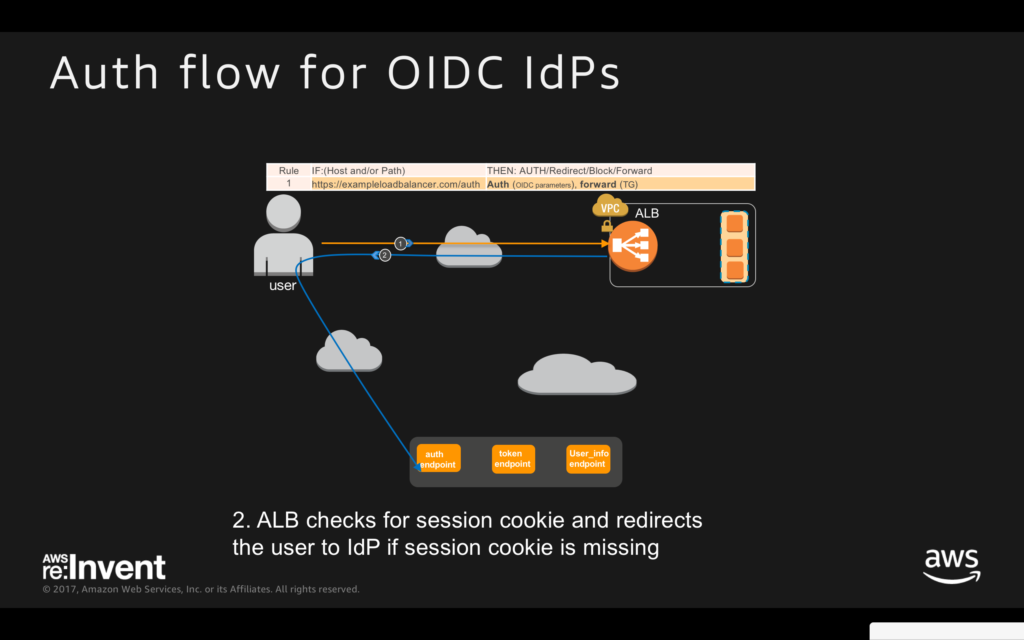
An Application Load Balancer (ALB) can be used to authenticate users in a few different ways. One option is using the ALB’s built-in authentication feature, which allows you to authenticate users before they access your application.
To use this feature, you’ll need to set up an authentication action and then configure a listener rule that references the action. The authentication action can be configured to use either Amazon Cognito or an OpenID Connect-compatible identity provider for user authentication.
Another option is using client certificate authentication with the ALB. This method involves configuring SSL/TLS certificates on both the client side and server side of the connection, allowing for mutual TLS (mTLS) authentication.
With MLS, clients must present a valid SSL/TLS certificate when connecting to the ALB, which can then pass along information from that certificate to your back-end servers as part of the request headers.
There are several options available for using an Application Load Balancer to authenticate users depending on your specific needs and security requirements.
The advantages and disadvantages of using an Application Load Balancer for authentication
Using an Application Load Balancer (ALB) for authentication has its advantages and disadvantages. One of the main benefits is that it can provide a centralized location for authenticating users, which simplifies the management of user credentials across different services.
Additionally, ALBs can help to distribute traffic more evenly, reducing the chances of overloading a single server with too many requests. They can also improve security by filtering out malicious requests before they reach backend servers.
However, there are also some drawbacks to using ALBs for authentication. For one thing, they may introduce additional latency due to the extra hop between clients and servers. Additionally, if not configured properly or secured adequately, they could become a single point of failure or open up new attack vectors.
It’s important to weigh these pros and cons carefully when deciding whether or not to use an ALB for authentication in your application architecture. You may find that another method such as OAuth 2.0 or SAML might be better suited depending on your specific needs and constraints.
Other methods of authenticating users
While using an Application Load Balancer to authenticate users can be effective, other methods can achieve this same goal. One such method is to use a reverse proxy server, which sits between the client and the web application and handles authentication requests.
Another option is to use a dedicated authentication service, such as OAuth or OpenID Connect. These services allow users to authenticate with one set of credentials across multiple applications.
Additionally, some web frameworks have built-in authentication features that allow for user management directly within the application code. This can be useful for smaller applications where external services may not be necessary.
It’s important to consider the specific needs and requirements of your application when choosing an authentication method. Some factors to consider include security requirements, scalability needs, and ease of implementation.
Ultimately, whichever method you choose should provide secure access control while also being easy for users to navigate and ensuring minimal disruption to their experience interacting with your application.
Access logs for your Application Load Balancer
Access logs are a crucial aspect of monitoring and troubleshooting your Application Load Balancer (ALB). These logs contain information about incoming requests, which can help you identify issues such as high latency or errors.
To enable access logging for your ALB, you need to specify an Amazon S3 bucket where the logs will be stored. Once enabled, access logs will automatically be created and saved in this bucket.
The log files include details such as the time of each request, client IP address, target group ARN, response codes, and more. This data is valuable for analyzing traffic patterns and identifying potential security threats.
By using tools like Amazon Athena or Elasticsearch Service on AWS, you can easily query these logs to extract specific pieces of information that can help with troubleshooting or performance optimization.
It’s important to regularly review your access logs to ensure that they’re being generated properly and that there aren’t any unexpected spikes in traffic or suspicious activity. By proactively reviewing these records, you’ll be better equipped to address any issues before they turn into major problems.
Why can’t clients connect to my ELB load balancer?
If you’re having trouble connecting to your ELB load balancer, there could be a few reasons why. First, it’s important to ensure that you have the correct DNS name and port number when trying to connect. Double-check that these details are correct in your client configuration.
Another reason could be related to security groups. Make sure that your security group settings allow traffic from the IP addresses or ranges of IPs that will be accessing the load balancer.
If you’re using SSL/TLS encryption on your load balancer, check that the client is configured with compatible encryption protocols and ciphers.
It’s also possible that there may be an issue with one of the instances registered with the load balancer. Check for any errors or issues in these instances and make any necessary updates or fixes.
If none of these solutions work, consider checking AWS support for further troubleshooting assistance.
Conclusion
An Application Load Balancer can be a valuable tool for authenticating users in your web application. It provides a centralized point of control that can help simplify the authentication process and improve security. However, it’s important to consider the potential drawbacks, such as increased complexity and reduced flexibility.
If you choose to use an Application Load Balancer for authentication, be sure to carefully configure it according to best practices and regularly monitor logs for any suspicious activity. And if you encounter any issues along the way, take advantage of resources like AWS support or online communities to get the help you need.