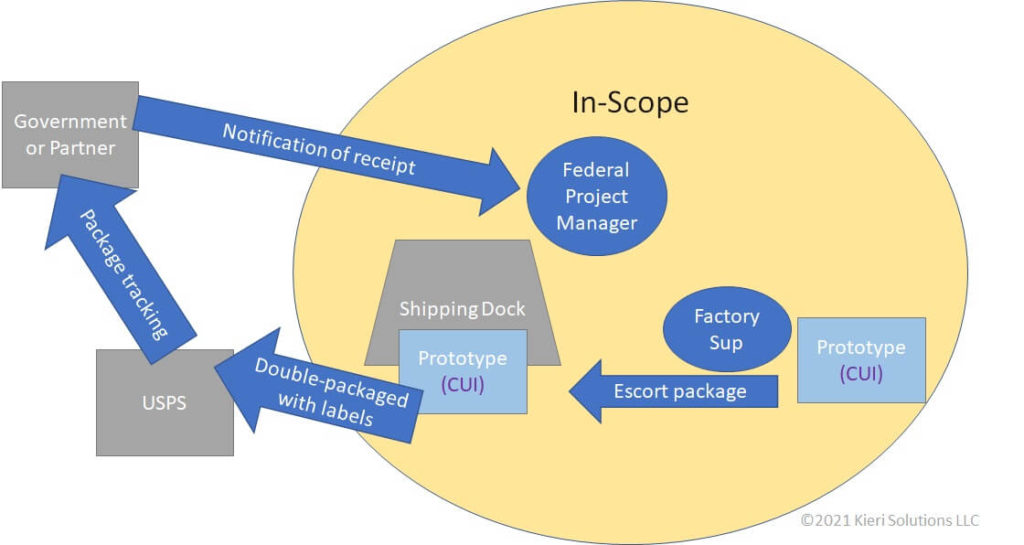
A lot of defense contractors think they’ve got their data under control—until a CMMC assessment puts it to the test. Knowing where your Controlled Unclassified Information (CUI) lives, moves, and rests isn’t just good practice anymore—it’s required. Without clear, documented CUI data flows, the best cybersecurity tools won’t mean much when it’s time to satisfy CMMC compliance requirements.
Validating CUI Traceability Across Your Network Boundaries
Data doesn’t stay in one place—it travels through routers, crosses virtual boundaries, and often ends up in unexpected systems. That’s where traceability matters. To meet CMMC level 2 requirements, every path your CUI takes needs to be documented and explainable. Assessors want to see exactly how data flows in and out of the environment, including external service providers or remote user access. If that information is unclear or missing, your compliance standing takes a hit.
● Identify each CUI entry point across systems, including third-party apps
● Track movement across network zones—internal, cloud, hybrid, or remote
● Show segmentation between systems that process CUI and those that don’t
Validating traceability isn’t a guessing game. It’s a chance to prove there’s no ambiguity in how CUI is protected. A well-mapped flow shows assessors that you’ve taken your data obligations seriously, and helps streamline the CMMC assessment process before it even begins.
Pinpointing Data Custodianship to Satisfy Assessor Requirements
A secure system is nothing without accountability. The CMMC framework expects organizations to clearly define who’s responsible for managing CUI at every stage. This isn’t limited to IT personnel—anyone with access to CUI becomes part of the picture. That means policies need to spell out ownership from creation to storage to transmission.
Assessors working with a C3Pao expect answers to questions like: “Who owns this data?” and “Who ensures its security controls are working?” If responsibility is unclear, that raises risk. Assigning specific custodians also boosts internal accountability, a key factor in meeting CMMC compliance requirements across levels.
Ensuring Data Lineage Visibility for Audit Readiness
Knowing where CUI originated—and where it’s been—is essential for audit readiness. Assessors want to follow a breadcrumb trail that reveals the full story of your data. That includes version changes, system transfers, and user interactions. A clean data lineage means fewer surprises and smoother assessments.
Visibility into data history also helps spot weak links. Maybe sensitive files moved through a less secure path, or backups were stored in outdated systems. This isn’t about assigning blame—it’s about correcting gaps before a CMMC assessment puts them under a microscope. CMMC level 2 requirements expect evidence, not assumptions.
Strengthening CUI Lifecycle Controls Before Formal Evaluation
From creation to deletion, CUI must be monitored, protected, and eventually disposed of properly. But too often, lifecycle policies stop at access control. Stronger controls mean knowing not just who accessed a file, but how long it was retained, how it was archived, and whether deletion processes are enforceable.
The lifecycle should include:
● Controlled creation with access tags or encryption
● Storage with retention rules tied to contract obligations
● Verified deletion logs for systems holding expired CUI
Strengthening lifecycle management early allows organizations to meet CMMC level 1 requirements and prepare for more rigorous reviews later. It’s easier to adjust a policy than to fail an assessment.
Mapping Data Transfers to Clarify Compliance Posture
Data doesn’t only move inside one building anymore—it’s emailed, synced to cloud drives, and shared with partners. Each transfer must be reviewed to ensure it aligns with the organization’s CMMC compliance requirements. Mapping these transfers means creating a visual and logical overview of data handoffs—both internal and external.
This process helps clarify your compliance posture. It shows where protections are strong and where they might need tightening. Transfers to third-party vendors or through unsecured channels could trigger red flags in a CMMC assessment. Fixing those before the audit begins keeps your project timelines and reputation intact.
Documenting Data Transit Paths for Definitive CMMC Evidence
Documentation is the proof that makes or breaks a CMMC evaluation. Assessors don’t want guesses or verbal walk-throughs—they need clear, written paths showing how CUI moves through your system. These diagrams and process descriptions serve as a backbone of your CMMC package.
Well-documented transit paths demonstrate:
● That you’ve done the work to understand your system
● That your protections are based on real use-cases, not just templates
● That your team can quickly respond if data ever goes where it shouldn’t
Even if the system is secure, poor documentation can lead to failed assessments. The effort put into clarity now saves weeks of backtracking later.
Securing Data Interchanges to Fortify Assessment Confidence
Every place where data leaves or enters your environment needs protection—those are the pressure points assessors focus on. This includes API connections, file transfers, collaboration platforms, and email servers. If those interchanges are unsecured or under-documented, they become liabilities.
Securing these interchanges shows your team has thought through every entry and exit. Encrypting data in transit, using MFA on all portals, and restricting file sharing are good starting points. But the goal isn’t just good security—it’s confidence. The c3pao reviewing your system is more likely to sign off on your CMMC assessment if they see attention to detail in places others overlook.